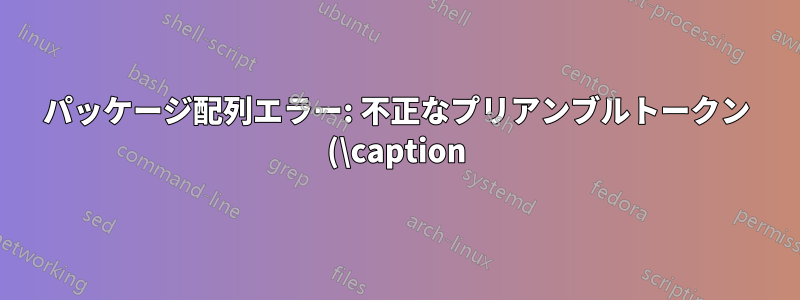
%3A%20%60c'%20%E3%81%8C%E4%BD%BF%E7%94%A8%E3%81%95%E3%82%8C%E3%81%A6%E3%81%84%E3%81%BE%E3%81%99.png)
このエラーに遭遇しました
Package array Error: Illegal pream-token (\caption): `c' used."
修正を手伝ってください。ありがとうございます
\documentclass[a4paper,11pt]{article}
\usepackage[english]{babel}
\usepackage[letterpaper,top=2cm,bottom=2cm,
left=3cm,right=3cm,marginparwidth=1.75cm]{geometry}
\usepackage{amsmath}
\usepackage{longtable}
\usepackage{afterpage}
\usepackage{tabularx}
\usepackage{caption}
\usepackage{array}
\usepackage{graphicx}
\usepackage{makecell}
\afterpage{
\begin{longtable}[h!]
\caption{Table 1: Features comparison}
\label{tab:my_label} \\
\begin{tabularx}{\textwidth}{|%
>{\centering\arraybackslash}X|>{\centering\arraybackslash}X|
>{\centering\arraybackslash}X|>{\centering\arraybackslash}X|
>{\centering\arraybackslash}X|>{\centering\arraybackslash}X|}
\hline
Authors & Topic & Scalability & Comparison & Theoretical Value & Application\\
\hline
\cite{alzahrani2018detection}Alzahrani et al. 2018 & DDoS attack & No & No & No & \\
\hline
\cite{biggio2011support}Biggio et al. 2011 & Adversarial attack & No & No & No & \\
\hline
\cite{biggio2012poisoning}Biggio et al. 2012 & Poisoning attacks & No & No & No & \\
\hline
\cite{chen2018detecting}Chen et al. 2018 & Activation clustering & No & No & No & \\
\hline
\cite{fredrikson2015model}Fredrikson et al. 2015 & Inversion attacks & No & No & No & \\
\hline
\cite{fredrikson2014privacy}Fredrikson et al. 2014 & Inversion attacks & No & No & No & \\
\hline
\cite{goodfellow2014explaining}Goodfellow, et al. 2014 & & & & & \\
\hline
\cite{gu2017badnets}Gu, et al. 2017 & & & & & \\
\hline
\cite{hu2021artificial}Hu, et al. 2021 & & & & & \\
\hline
\cite{jaszcz2022aimm}Jaszc, et al. 2022 & & & & & \\
\hline
\cite{alzahrani2018detection}Alzahrani et al. 2018 & DDoS attack & No & No & No & \\
\hline
\cite{biggio2011support}Biggio et al. 2011 & Adversarial attack & No & No & No & \\
\hline
\cite{biggio2012poisoning}Biggio et al. 2012 & Poisoning attacks & No & No & No & \\
\hline
\cite{chen2018detecting}Chen et al. 2018 & Activation clustering & No & No & No & \\
\hline
\cite{fredrikson2015model}Fredrikson et al. 2015 & Inversion attacks & No & No & No & \\
\hline
\cite{fredrikson2014privacy}Fredrikson et al. 2014 & Inversion attacks & No & No & No & \\
\hline
\cite{goodfellow2014explaining}Goodfellow, et al. 2014 & & & & & \\
\hline
\cite{gu2017badnets}Gu, et al. 2017 & & & & & \\
\hline
\cite{hu2021artificial}Hu, et al. 2021 & & & & & \\
\hline
\cite{jaszcz2022aimm}Jaszc, et al. 2022 & & & & & \\
\hline
\end{tabularx}
\end{longtable}
}
\afterpage{
\bibliographystyle{splncs04}
\bibliography{splncs04}
}
\end{document} %This is the error location
答え1
tabularx環境の中に環境を入れ子にしてはいけませんlongtable。また、longtableはフロートではないため (LaTeX 固有の意味では)、 などの位置指定子を指定しても意味がありません[h!]。
あなたが実際に利用したいのは、環境xltabular(xltabularlongtableパッケージ)は、との機能を組み合わせたものtabularxで、単一環境. とxltabular同様にtabularx、 は二引数: (i) ターゲットの幅 (ここでは\textwidth) と (ii) 列仕様のグループ。
\documentclass[a4paper,11pt]{article}
\usepackage[english]{babel}
\usepackage[letterpaper,vmargin=2cm,hmargin=3cm,
marginparwidth=1.75cm]{geometry}
\usepackage{amsmath}
%\usepackage{longtable}
%\usepackage{tabularx}
%\usepackage{array}
\usepackage{xltabular}
\newcolumntype{C}{>{\centering\arraybackslash\hspace{0pt}}X} % centered
\newcolumntype{L}{>{\raggedright\arraybackslash\hspace{0pt}}X}% left-aligned
\usepackage{caption}
\begin{document}
\setlength\extrarowheight{2pt} % for a less-cramped "look"
\begin{xltabular}{\textwidth}{|L|C|c|c|C|C|}
% headers and footers
\caption{Comparison of features} \label{tab:my_label} \\
\hline
Authors & Topic & Scalability & Comparison & Theoretical Value & Application\\
\hline
\endfirsthead
\multicolumn{6}{l}{\tablename\ \thetable, continued} \\[1ex]
\hline
Authors & Topic & Scalability & Comparison & Theoretical Value & Application\\
\hline
\endhead
\hline
\multicolumn{6}{r}{\footnotesize (continued on next page)}\\
\endfoot
\endlastfoot
% body of table
\cite{alzahrani2018detection}Alzahrani et~al.\ 2018 & DDoS attack & No & No & No & \\
\hline
\cite{biggio2011support}Biggio et~al.\ 2011 & Adversarial attack & No & No & No & \\
\hline
\cite{biggio2012poisoning}Biggio et~al.\ 2012 & Poisoning attacks & No & No & No & \\
\hline
\cite{chen2018detecting}Chen et~al.\ 2018 & Activation clustering & No & No & No & \\
\hline
\cite{fredrikson2015model}Fredrikson et~al.\ 2015 & Inversion attacks & No & No & No & \\
\hline
\cite{fredrikson2014privacy}Fredrikson et~al.\ 2014 & Inversion attacks & No & No & No & \\
\hline
\cite{goodfellow2014explaining}Goodfellow et~al.\ 2014 & & & & & \\
\hline
\cite{gu2017badnets}Gu et~al.\ 2017 & & & & & \\
\hline
\cite{hu2021artificial}Hu et~al.\ 2021 & & & & & \\
\hline
\cite{jaszcz2022aimm}Jaszc et~al.\ 2022 & & & & & \\
\hline
\cite{alzahrani2018detection}Alzahrani et~al.\ 2018 & DDoS attack & No & No & No & \\
\hline
\cite{biggio2011support}Biggio et~al.\ 2011 & Adversarial attack & No & No & No & \\
\hline
\cite{biggio2012poisoning}Biggio et~al.\ 2012 & Poisoning attacks & No & No & No & \\
\hline
\cite{chen2018detecting}Chen et~al.\ 2018 & Activation clustering & No & No & No & \\
\hline
\cite{fredrikson2015model}Fredrikson et~al.\ 2015 & Inversion attacks & No & No & No & \\
\hline
\cite{fredrikson2014privacy}Fredrikson et~al.\ 2014 & Inversion attacks & No & No & No & \\
\hline
\cite{goodfellow2014explaining}Goodfellow et~al.\ 2014 & & & & & \\
\hline
\cite{gu2017badnets}Gu et~al.\ 2017 & & & & & \\
\hline
\cite{hu2021artificial}Hu et~al.\ 2021 & & & & & \\
\hline
\cite{jaszcz2022aimm}Jaszc et~al.\ 2022 & & & & & \\
\hline
\end{xltabular}
\end{document}



